TAIWAN LINE TEK ELECTRONIC CO.,LTD.| Information Security Policy
LINETEK (hereinafter referred to as "the Company"), in order to ensure the security of information, systems, equipment, and network communications, and to effectively reduce risks of theft, misuse, leakage, alteration, or damage to information assets caused by human error, malicious acts, or natural disasters, has established an Information Security Management System. Accordingly, the Company hereby formulates this Information Security Policy (hereinafter referred to as "this Policy") to ensure the confidentiality, integrity, and availability of information.
1.Confidentiality:
Ensure that only authorized personnel are allowed to access sensitive information.
2.Integrity:
Ensure that the information in use is accurate and has not been altered or tampered with.
3.Availability:
Ensure that authorized users are able to access information and related information assets whenever needed.
This Information Security Policy applies to all employees of the Company, including contract staff and outsourced maintenance/service providers.
Objectives:
1.Establish an Information Security Steering Committee responsible for promoting and overseeing information security initiatives.
2.Evaluate personnel appointments and assignments. For employees who resign, take leave, are suspended, or are transferred, appropriate control and workforce backup measures shall be established. Additionally, regular information security education and awareness programs shall be conducted to enhance personnel's understanding and proficiency in information security.
3.Establish an information asset management system to effectively allocate, utilize, and manage information resources.
4.Enhance computer network defense capabilities to timely prevent external intrusions and damages.
5.Establish an information security audit system to conduct regular or ad hoc audits of all computer systems, and strictly prohibit the deletion or modification of any audit records.
Organizational Structure:
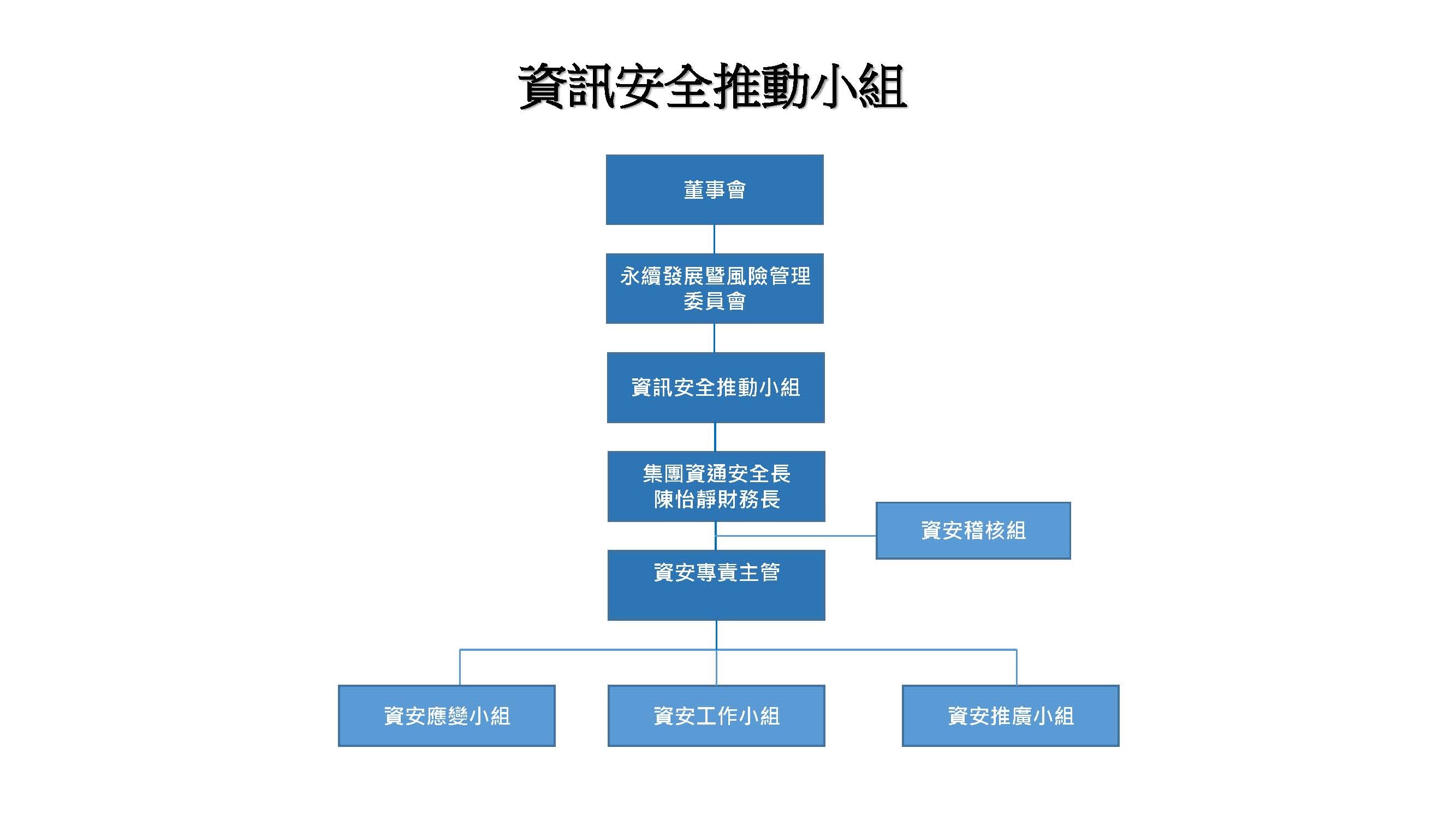
Concrete Strategic Plan:
Our company has proposed concrete information security strategies from four perspectives: policy, institutional framework, protective capability, and education & training.
1.Promotion of Information Security Policies: The company’s Information Security Executive Committee, composed of the Chief Information Security Officer (CISO) and department heads, oversees the planning and implementation of security strategies to ensure the effective promotion and enforcement of information security policies.
2. Enhancing Information Security Governance Maturity: The company has implemented the ISO 27001 Information Security Management System, establishing an information security management framework that meets international standards. On October 21, 2025, the company received the notification of successful certification and is currently awaiting the official certificate issuance.
3. Strengthening Technical Security Measures: The company has joined the TWCERT Information Security Alliance to enhance overall information security protection and incident response capabilities. At the same time, the ISO 27001 management system has been integrated for a comprehensive review and strengthening of technical security measures.
4.Employees are notified to remain vigilant and to cooperate whenever there are major software updates or significant information security threat incidents.
5.The company has purchased cyber insurance to enhance information security resilience. Considering operational risks, appropriate insurance products should be selected to effectively transfer potential information security loss risks, ensuring stable business operations and sustainable development. The evaluation is currently ongoing.
Resources Allocated to Information and Communication Security Management:
The company actively invests in information security, allocating relevant personnel and equipment to plan, monitor, and implement information security policies. The measures taken and the results achieved are as follows:
1. In 2025, the ISO 27001 Information Security Management System was fully implemented, and the company successfully passed the official certification in October 2025.
2. The Information Security Executive Committee meetings are held periodically. In 2025, a total of two meetings were conducted, with the Chief Information Security Officer, a dedicated security manager, and two dedicated security personnel in attendance.
3. Endpoint hardware and software devices, including firewalls, vulnerability scanners, antivirus software for computers and emails, and spam filtering network devices.
4. Strengthening access control for information and communication systems and related devices by conducting account and permission audits, applying the principle of least privilege, enhancing password management mechanisms, and implementing logging and auditing of system administration activities to prevent unauthorized system operations.
5. Strengthening the protection and monitoring of the company’s local area network and related devices by implementing a segmented network architecture. Physical firewall devices are used to isolate information service zones, separating equipment of different importance and risk levels. Access permissions between zones are restricted to reduce the risk of lateral movement by malicious programs, and activity audits are enhanced to ensure continuous monitoring and prevention.
6. Enhancing employees’ information security awareness by conducting annual information security training courses. As of October 31, 2025, a total of 106 participants attended, accumulating 467 hours of training. Employees are also notified to remain vigilant and cooperate during major software updates or information security threat incidents.
Information Security Risks and Countermeasures:
The company has established network and computer-related information security measures and continuously reviews and evaluates its information security policies and procedures to ensure their appropriateness and effectiveness. With the rapid development of digital technologies, threats such as ransomware attacks and social engineering scams are increasingly prevalent. These cyberattacks may attempt to breach the company’s external websites and mail servers, potentially compromising or attempting to steal confidential company information. In the event of a severe cyberattack, the company may lose critical data, and external communications could be disrupted. Malicious hackers may also attempt to introduce computer viruses, destructive software, or ransomware into the company’s network systems, which could interfere with operations or be used for extortion. To mitigate potential hacker intrusions, ransomware, and DDoS/APT attacks, the company continuously monitors external information security events, absorbs new knowledge to strengthen security controls, and maintains multi-layered protection and incident response mechanisms. Additionally, efforts are made to raise information security awareness among employees to effectively respond to cyberattack threats.
Information Security Implementation Results:
As of October 2025, no information security incidents affecting the company’s operations have occurred.
Certificate:


